I ROUTER WORKSTATION N +--------------+ +--------------+ T | | LAN1 | | SUBJECT E WAN | 192.168.0.1<-------> (enp0s31f6)192.168.0.102 | +------------+ R <=======> | | | | LAN2 | | N | | | 10.0.0.1(enp13s0) <-------> (eno1)10.0.0.2 | E | | | | | | T +--------------+ +--------------+ +------------+Spot the (multiple) problems here?
SUBJECT can't reach the 'Net. In fact, it's worse: because private network addresses aren't intended to be routed, the router serving 192.168.0.0/24 quite properly won't even respond to pings from SUBJECT inside 10.0.0.0/24. Without attention to normally ignored configuration details SUBJECT is an island.
There is nothing (no DHCP) on 10.0.0.0/24 to service enp13s0, so it needs a static configuration:
iface enp13s0 inet static address 10.0.0.1/24...to /etc/network/interfaces and issue...
sudo ifup enp13s0And possibly add "auto enp13s0" to the interfaces file if you want it brought up all the time automatically.
interface=enp13s0...so it only pays attentions to queries arriving on the secondary (enp13s0) ethernet port. This way dhcpcd (which is part of most distros' installers) on SUBJECT gets its configuration automatically on boot, but, as simple as dnsmasq is, that's still more configuration!
So sometimes I just `sv stop dhcpcd` and use the ip tool to slam a static configuration into SUBJECT.
ip address add 10.0.0.2 dev eno1 ip route add default via 10.0.0.1 dev eno1 ip address del 169.254.x.x/16 dev eno1...and an editor to paste...
nameserver 75.75.75.75...into /etc/resolve.conf.
If SUBJECT is ever fully setup and moved elsewhere on my network it will get its address, default route, and nameserver from whatever is providing DHCP to that network.
sysctl -w net.ipv4.ip_forward=1Alternatively, edit the same entry in /etc/sysctl.conf and issue...
sysctl -p...to reload. Obviously, editing sysctl.conf is a permanent (until you change it back) approach.
Host WORKSTATION needs to do source network address translation (NAT). Using the (newer) nft interface to the kernel packet handling stack...
nft add table nat
nft 'add chain nat postrouting { type nat hook postrouting priority 100; }'
nft add rule nat postrouting ip saddr 10.0.0.0/24 oif enp0s31f6 snat to 192.168.0.102
nft list ruleset
Replace "enp0s31f6" and the IP addresses with your own!
That last line isn't required; it just shows how you have configured the kernel:
table ip nat {
chain postrouting {
type nat hook postrouting priority srcnat; policy accept;
ip saddr 10.0.0.0/24 oif "enp0s31f6" snat to 192.168.0.102
}
}
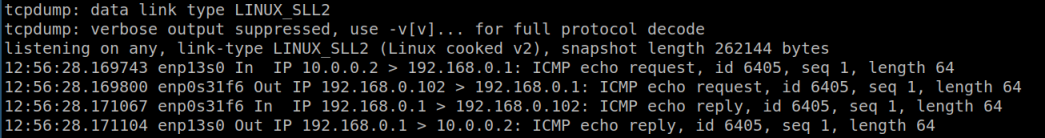
You should now be able to ping the router from SUBJECT.
tcpdump -i any -n...on WORKSTATION and watch the 4-part dance of a ping.
